Architect Ryan
nClam: A .NET library to virus scan
📅 May 19, 2011 ⏱ 3 min read
Here is a very common scenario: You have an ASP.NET website (WebForms or MVC). It has a feature that accepts a file upload from your users. Other visitors of your site are then able to download that file to their computer.
You might ask, is there a problem with this scenario? Well, I would say, probably. If a user uploads an infected file to your website, you will be essentially distributing that infected file to any of your other potential visitors. That’s not good. So what can you do? Scan that upload with a virus scanner!
I’ve done a lot of research and unfortunately found that there are very few libraries for .NET which allow on-demand scanning. There are a couple that have a $1k+/year price tag and while they might have good features, it seems extremely pricy for virus scanning some file uploads. There is however, a really great open source antivirus engine called ClamAV. It looks like in the past there have been some efforts of making a ClamAV client for .NET, however the projects I found seem years old and I could not find anything that worked out of the box. So I went to work.
I had a prototype of nClam, a pure .NET client to ClamAV, ready in a few hours. From there I polished up the code, added documentation, pushed it up to GitHub, and published a package to Nuget.
Using nClam is very easy. It has one pre-requisite, a ClamAV server. In the past, ClamAV was difficult to get running on Windows, but the team has done a lot of work on the Windows version and it’s able to install as a Windows Service right out of the box now. Here are some quick steps to installing ClamAV:
- Download the 32-bit or x64 version of ClamAV here: http://oss.netfarm.it/clamav/.
- Extract the ClamAV binaries to
C:\\clamav - Create an empty folder called
DBinC:\\clamav
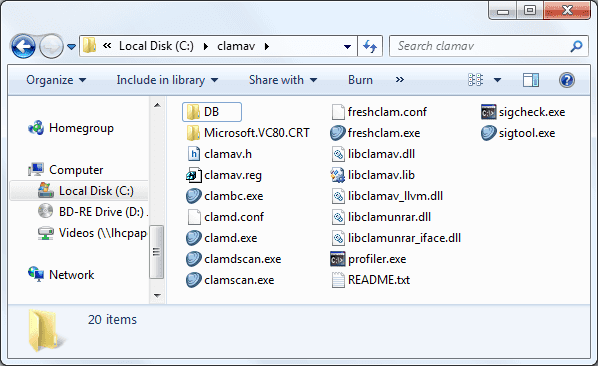
- From a command prompt in
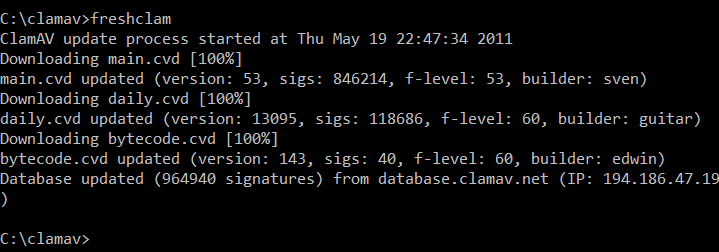
C:\\clamav, runfreshclam.exe(this will download the latest virus definitions)
- Install the ClamAV service by running:
clamd --install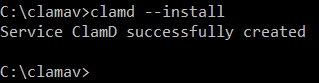
- Install the ClamAV Virus Updater service by running:
freshclam --install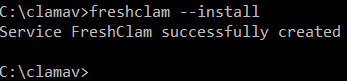
- Open up the Windows Services list and set the “ClamWin Free Antivirus Scanner Service” and the “ClamWin Free Antivirus Database Updater” to Startup Type: Automatic and start them.
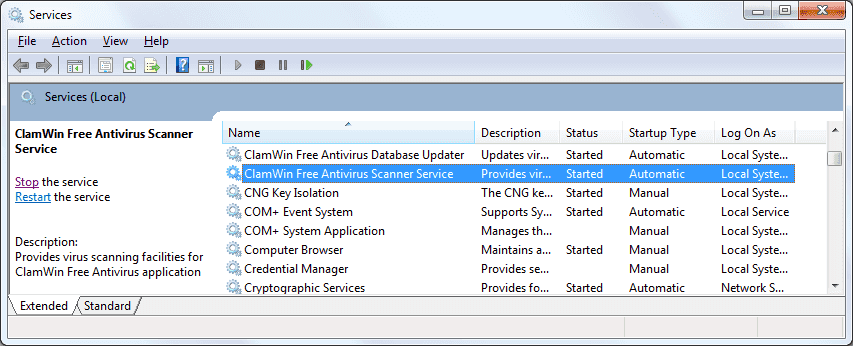
- The ClamAV Server is now set up!
Once ClamAV is running, you can now on-demand scan anything from code using nClam. Using nClam is easy! First, get the nuget package nClam (or download it from github) and reference it in your project. From there, instantiate a ClamClient object with the location of your server (which is probably localhost at this point) and the port it is running under (default is 3310) and call one of the Scan methods! These methods return a ClamScanResult object, which has a handy enum which tells you if your scan was clean or a virus was detected. Here is some sample code:
var clam = new ClamClient("localhost", 3310);
var scanResult = clam.ScanFileOnServer("C:\\test.txt"); //any file you would like!
switch (scanResult.Result)
{
case ClamScanResults.Clean:
Console.WriteLine("The file is clean!");
break;
case ClamScanResults.VirusDetected:
Console.WriteLine("Virus Found!");
Console.WriteLine("Virus name: {0}", scanResult.InfectedFiles.First().VirusName);
break;
case ClamScanResults.Error:
Console.WriteLine("Woah an error occured! Error: {0}", scanResult.RawResult);
break;
}nClam is free and open source. It is published under the very open Apache 2 license. Here are some links to get nClam:
- nClam GitHub Project Page: https://github.com/tekmaven/nClam (click the big download button on the right side for a binary release!)
- nClam Issue Tracker: https://github.com/tekmaven/nClam/issues
- nClam Nuget Package: http://nuget.org/List/Packages/nClam
As always, I would love some feedback on this. Feel free to post this to your blogs, tweet about it, and share it to any .NET developer. Let’s make our applications more secure!
Written by Ryan Hoffman, an experienced team leader, certified Scrum Master and software architect.
Contact RyanFollow Ryan on Twitter
The postings on this site are my own and I am not speaking as a representative of my employer, any company or organization.